
I’m assuming you are using a Microsoft CA for this exercise. Technically you can use any CA, so don’t think that you are just limited to Microsoft’s implementation. Certificates are standardized in the X.509 format. In a real enterprise environment CAs should be heavily locked down and you probably won’t have permissions to change anything on the CA. Find your CA administrator and have them complete this section. If you aren’t using a Microsoft CA, then the steps below won’t exactly apply to you. But research how to configure your CA for the “required” properties.
Blog Series
SQL 2012 AlwaysOn Failover Cluster for vCenter
vSphere 5.5 Install Pt. 1: Introduction
vSphere 5.5 Install Pt. 2: SSO 5.5 Reborn
vSphere 5.5 Install Pt. 3: vCenter Upgrade Best Practices and Tips
vSphere 5.5 Install Pt. 4: ESXi 5.5 Upgrade Best Practices and Tips
vSphere 5.5 Install Pt. 5: SSL Deep Dive
vSphere 5.5 Install Pt. 6: SSL Certificate Template
vSphere 5.5 Install Pt. 7: Install SSO
vSphere 5.5 Install Pt. 8: Online SSL Minting
vSphere 5.5 Install Pt. 9: Offline SSL Minting
vSphere 5.5 Install Pt. 10: Update SSO Certificate
vSphere 5.5 Install Pt. 11: Install Web Client
vSphere 5.5 Install Pt. 12: Configure SSO
vSphere 5.5 Install Pt. 13: Install Inventory Service
vSphere 5.5 Install Pt. 14: Create Databases
vSphere 5.5 Install Pt. 15: Install vCenter
vSphere 5.5 Install Pt. 16: vCenter SSL
vSphere 5.5 Install Pt. 17: Install VUM
vSphere 5.5 Install Pt. 18: VUM SSL
vSphere 5.5 Install Pt. 19: ESXi SSL Certificate
Permalink to this series: vexpert.me/Derek55
Permalink to the Toolkit script: vexpert.me/toolkit55
Certificate Template
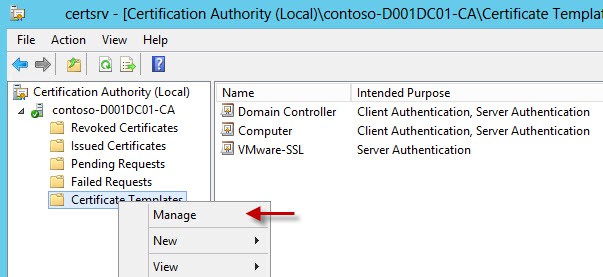
1. Logon to your Microsoft root CA. In this case I’m using Windows Server 2012. Launch the Certification Authority console. I’ve already created a custom template, VMware-SSL. But ignore that for now (just like a cooking show I have my template already done in the oven) and locate the Certificate Template container. Right click and select Manage.
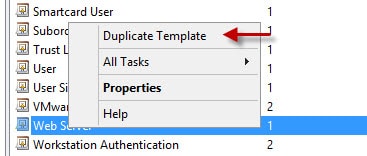
2. Locate the Web Server template, right click and duplicate it.
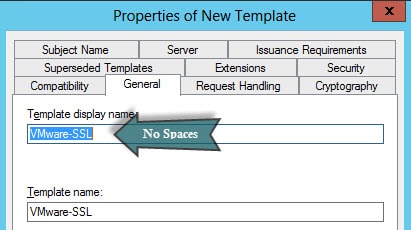
3. Don’t change anything on the compatibility tab. Don’t think you are clever and try changing the default value to something like Windows Server 2012. #Fail. On the General tab rename the template. I like using VMware-SSL because it has no spaces, so the template name and display name are the same. This avoids confusion down the road where a script requires the template name as a parameter. Spaces are allowed, but let’s not confuse the situation anymore than needed…we are already confused enough.
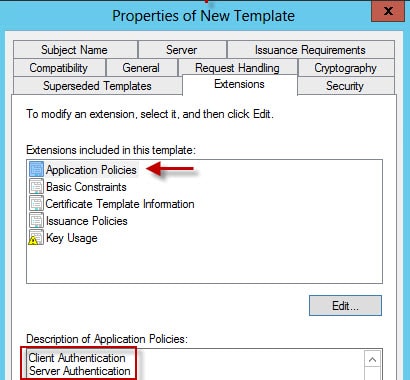
4. Click on the Extensions tab then highlight Application Policies. Click Edit and add Client Authentication.
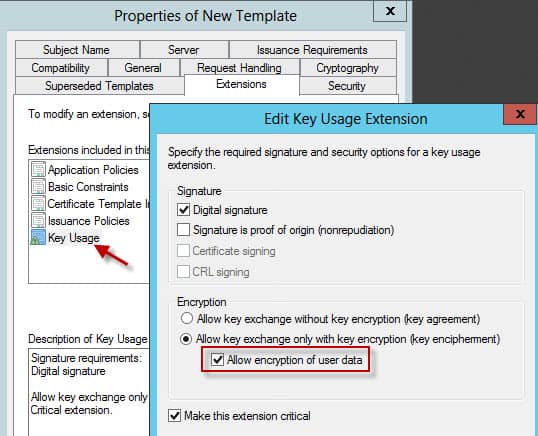
5. Click on Key Usage and check the box to allow encryption of user data. Close out of all the certificate properties windows.
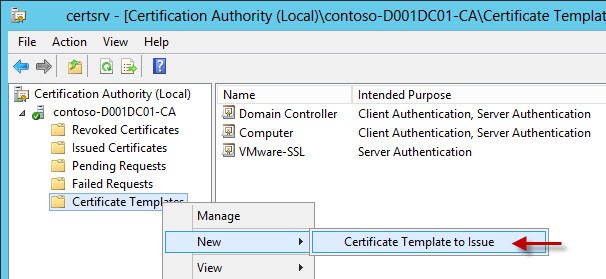
6. Back in the CA window issue the new VMware-SSL template, by selecting the menu item shown below. A list of available templates will appear, and just click on VMware-SSL. It should now appear in the right pane, as you can see below. Sometimes CAs can be slow, and it could take a couple of minutes to appear. Do not panic; be patient. Once it appears you now have a good template to use for VMware certificates (vCenter, ESXi hosts, etc.).
Summary
Creating a certificate template is not tricky and only takes a couple of minutes. It may take a few minutes for the new certificate type to replicate in AD. So don’t be too surprised if you can’t immediately see it. The steps are pretty much the same on Windows Server 2008 and later, so don’t worry if you aren’t yet using Windows Server 2012.
In Part 7 we (finally) get to mount the vCenter 5.5 ISO and install the SSO service. So yes, this install series is finally getting to the point were we can install something. But hopefully you are better educated about vCenter 5.5 than you were before you stumbled on this series. Impress your friends at your next cocktail party about SSL OU values and PEM files.




Derek, I just wanted to say thank you, this series has been a real asset as a consultant. ~Chris R
Derek – your blog is god sent to me right now! Thank You…. i am a newbie in the VM World and am trying setup VCenter in my organisation – and am stuck at the part where i need to generate a Certificate for SSO.
I'm currently clueless right now, as we do not have a MS CA server in our AD and i have not had any luck in finding a resource on generating a self signed certificate to proceed further in your guide.
can you please help guide what my options are?
Thank You,
Vikram
Vikram, thanks for the comments. My SSL tool assumes that there is a trusted root CA in your organization. It could be from Microsoft, OpenSSL, or something else. The software installs with self-signed certificates, so if that is what you are after then you are set. Only if you want fully trusted certificates do you need to use my SSL toolkit and follow additional procedures.
Oh cool, that means i can jump right away to part 11 of the guide… installing the web client…correct me if am wrong..
Yes
Hello
when i use your script to change SSL certificates it goes well but i receive a message saying im using a SHA1 certificate and i should use SHA2 instead. Is something ok or better to recreate with SHA2?
you want to create with SHA256 as SHA1 is not recommended (still the default for a 2008 template tho!)
If you are using SHA256, doesn’t the compatibility need to be changed to Certification Authority: Windows Server 2012 and Certificate Recipient: Windows 8 / Windows Server 2012?
I'm either doing a lot wrong or this article is severely lacking in detail. Here are my concerns:
1. We have many forests, vCenters and one Microsoft CA. Online minting is not possible without setting up Web Enrollment.
2. The script needs to be run from the vCenter… And where SSO is installed…
3. Microsoft Standalone CA doesn't support cert templates? Or maybe just 2008 R2 standalone CA.
4. You need an MS Enterprise CA to support the above?
I'm still struggling through this, but this is my experience so far.
Yes web enrollment is required for the online minting, and is a normal part of a CA deployment in my experience. The script requires some vCenter/SSO components, so as stated in the article it does need be run from a vCenter/SSO server. As far as I know all MS CAs support templates..I have not seen a version that does not. I have not tried the solution with a standalone MS CA, as my lab used an online enterprise CA. You need not use the online mode, and can have the tool merely create the SSL CSRs which you can manually… Read more »