Recently I’ve been re-doing my home network, and I’m now using the OPNsense firewall, replacing my Ubiquiti EdgeRouter 12 with a more robust solution. For OPNsense I selected the PROTECTLI FW6D platform, which has 6 ports and an Intel i5-8250U CPU. I’ve also been running Pi-Hole on my network for a while, as a way to block ads, spyware, and trackers. However, I wanted a new solution that relied less on home infrastructure yet still gave me good DNS-based ad, tracker, and spyware protection.
To that end, I’ve settled on retiring Pi-hole, and using NextDNS as a cloud based DNS filtering solution. It’s free up to 300,000 queries a month, or $20/year for home use for unlimited queries. NextDNS is highly configurable, supports DNS-over-TLS, DNS-over-HTTPS, for fully encrypted DNS queries. They also have an extensive list of block lists to choose from, such as cryptojacking protection, typosquatting protection, plus dozens of other block lists for ads, tracking, etc.
For my updated home network I wanted to point all my internal clients to OPNsense’s LAN IP for DNS, then have the NextDNS client CLI running on OPNsense that would receive all the LAN DNS queries, then forward them all to the NextDNS cloud for filtering and resolution.
These instructions assume you’ve already signed up for a NextDNS account, and have a configuration ID. The signup is simple, so I won’t screenshot that process. But do that prior to starting this how-to guide.
Installing and Configuring NextDNS
OPNsense comes bundled with Unbound DNS, which is a DNS service that forwards queries to the internet for resolution. I prefer simple solutions, so on my network I wanted the NextDNS client it be listening on port 53 on the LAN side of my OPNsense firewall, not Unbound. Theoretically you could have NextDNS listening on something like port 5353, and have Unbound on port 53 forwarding to the NextDNS client on 5353. However, I didn’t see many advantages of that solution for my network.
- SSH into OPNsense, open a shell, and run the following command:
sh -c 'sh -c "$(curl -sL https://nextdns.io/install)"'
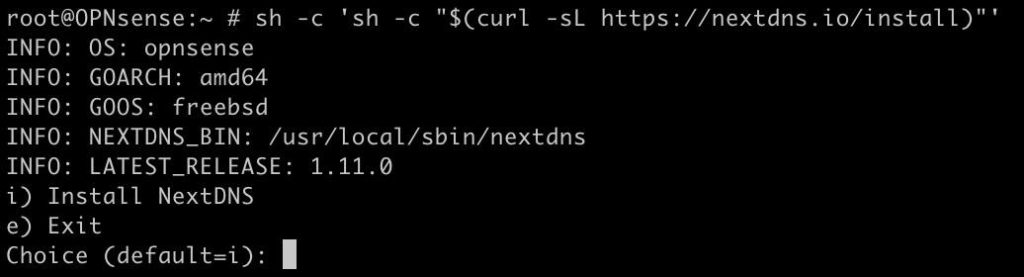
2. Type i for install
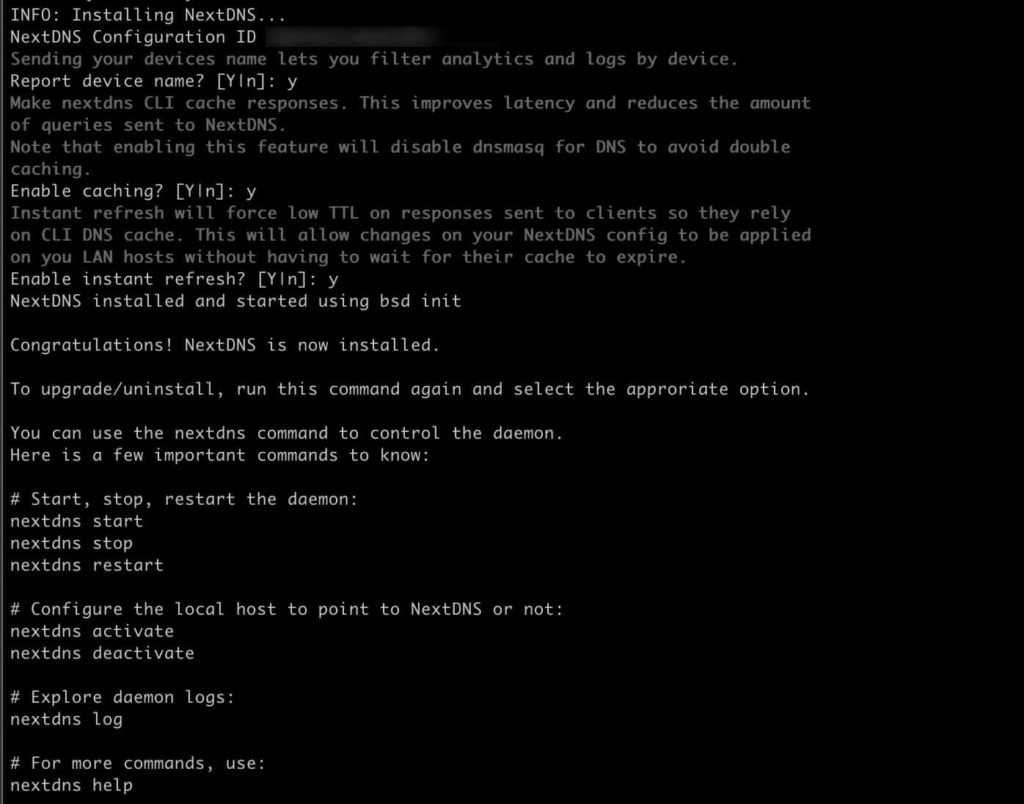
3. Answer the installer questions as you see fit. Have your NextDNS configuration ID handy. I answered Y to all the questions.
 ****************@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" />
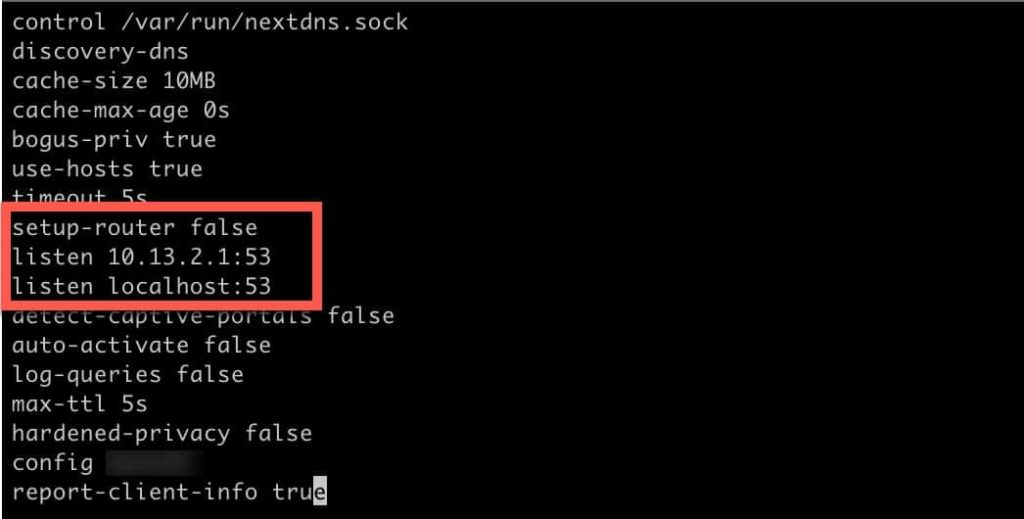
****************@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" /> 4. Edit nextdns.conf file and modify the parameters highlighted in the screenshot.
vi /usr/local/etc/nextdns.conf
5. Change setup-router to false.
6. Add a ‘listen‘ line with the LAN IP address of your OPNsense firewall, where you point the clients to for DNS, and add a colon 53 (:53) at the end.
7. Make sure the localhost line is also configured for port 53.
 **********************@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" />
**********************@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" /> 8. Save the NextDNS configuration file (<escape> :wq!).
9.Open the OPNsense web GUI, and navigate to: Services, Unbound DNS, General.
10. Untick the Enable Unbound box, if already checked.
11. Back in the SSH session, type nextdns restart.
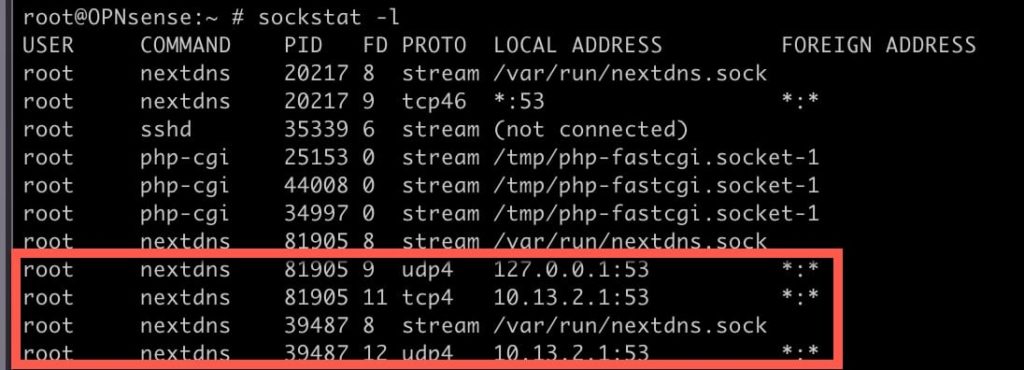
12. Type sockstat -l and look for NextDNS entries. You should see entries for your LAN IP and the loopback address, all listening on port 53.
13. You can also type nextdns log, and review the logs to ensure everything is running properly.
 **************@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" />
**************@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" /> 14. To validate name resolution is working, you can use the Drill command. One of the blocked domains in NextDNS is app-measurement.com. So if I run Drill against my OPNsense LAN IP, I should get 0.0.0.0 back:
drill app-measurement.com @10.13.2.1
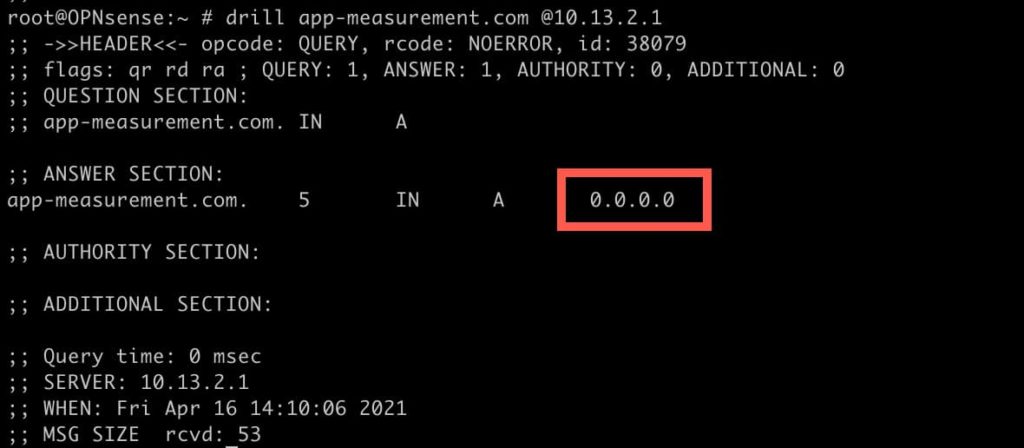 ***********@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" />
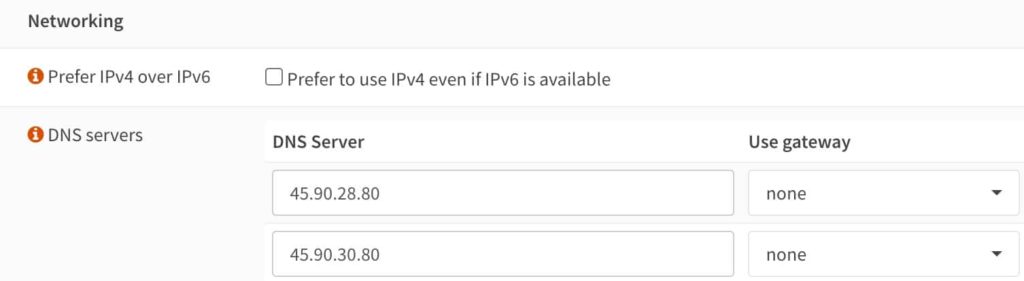
***********@**.jpg 600w" sizes="(max-width: 1024px) 100vw, 1024px" /> OPNSense DNS Settings
When configuring OPNsense, there are DNS settings in System -> Settings -> General. Here, I have entered the two NextDNS servers that are listed on the Setup page in your NextDNS account. Why? The primary reason why I configured these, vs. leaving them blank, is WireGuard. I have WireGuard installed on my OPNsense firewall, and in the boot sequence WireGuard comes up before the NextDNS CLI is started. Wireguard needs working name resolution to bring up WG0, so I have OPNsense using the NextDNS servers for name resolution.
Summary
Configuring OPNsense to use NextDNS is not hard, but does require modifying the default NextDNS CLI configuration file. After the NextDNS configuration is completed, your LAN clients can now use NextDNS without modification. This assumed they are already pointed at your OPNsense LAN IP for DNS, such as through DHCP.
You can also go to dnsleaktest.com from a LAN client, and validate that the client is using dns.nextdns.io. If the results show a DNS server other than NextDNS, something is wrong. You can also login to the NextDNS portal and review the DNS logs (if you’ve enabled them) to ensure queries from the LAN are being received.
 ********************@
********************@



Hi! Which hardware did you select for your opnsense?
I just updated the opening of the post to include my selection, which is the PROTECTLI FW6D.
Very nice – thank you. Do you know of a way to make this work for IPv6 queries as well? I tried adding ‘listen [::1]:53’ into the nextdns.conf file but it didn’t seem to work.
No, I don’t use IPv6 end to end so haven’t tried to make that work.
Question on Wireguard. Thanks for updating – so that I use the general settings: DNS Servers to enter my 2 NextDNS IPs…. until I did that I couldn’t get wireguard to work. The question is – the system>settings>general:DNS Servers for entering my DNS – is there a need to run the app on my router at all? What benefit would it have. My understanding is the NextDNS app doesn’t yet support OPNSense? How about using Unbound with NextDNS – I think it has the same issue with Wireguard – but even if it worked – there doesn’t seem to be… Read more »
Yes I don’t see any advantage in running Unbound with NextDNS. I did try and see if they would work together, and at least for me, Unbound kept throwing errors at random times, so I disabled it. Running the NextDNS CLI on OPNsense gives you more configuration options and also lets you log client data to NextDNS. So that’s better than merely putting in NextDNS servers into OPNsense and calling it a day.
Hi there
can i continue to use Unbound as i use it for host overrides etc. or is it mandatory that i disable it?
While you can technically use Unbound with the NextDNS client, I had issues getting them to play together nicely. Unbound was frequently giving me nxserver (I think) errors and not resolving hosts. Plus, I think if you use Unbound then NextDNS won’t be able to log all the client info in the logs, if that matters to you.
Does this method use TLS? If not does anyone know how to get that working?
How would one go about and enabling a local domain (plex.direct) using the nextdns CLI? In unbound I just add this to the Custom Options.
Hi !
Thanks for the writeup. I tried this to run on OPNSense 21.7.3 fresh install. The installation went OK but log file says Error: exit status 2
Thank you so much for creating the guide, Derek. It worked like a charm!
Been using my Pi-hole with Unbound for a long time and just recently upgraded my router/firewall to OPNsense. I was fortunate to discover NextDNS since Mullvad’s DNS over TLS was quite temperamental with the OPNsense’s Unbound.
Thanks again!
Thank you for the tutorial, and after following it, all seemed to work. But today i opened NextDNS control panel and it said that my computer (mac) was using 1.1.1.1 as dns server also showing a red dot, yesterday the dot was green. That was cloudflare DNS that i had configures in system -> Settings -> General when i first installed OPNSense. As I am not using wireguard i removed cloudflare dns servers but i immediately lost DNS resolving in my clients. So i added NextDNS servers in system -> Settings -> General The question is, is NextDNS CLI working… Read more »
would you happen to have instructions on autostarting the nextdns daemon after a restart?
You manage to get hostnames in the logs?
There is now an easier option, which is a single command: https://github.com/Control-D-Inc/ctrld/wiki/NextDNS-Mode