Session: BRK3130
Note: This was a great beginner level session for those not familiar with encryption, certificates or PKI. If you are in that boat, I would urge you to find the session video and watch the whole presentation. If you are a security professional and already know about these topics, then the content is probably too basic. I didn’t capture all the content below, but just took down some highlights what was covered.
Why am I here? Thanks to the NSA. Thanks to Edward Snowden. SharePoint, Lync, Exchange all need to be secure.
Shows screens of RDP SSL warnings, and browser SSL warnings.
Are you still using passwords? Phishing and fraud, password fatigue, pass the hash attacks
IoT (Internet of things) is adding new concerns of authentication (connected cars, medical, industrial sensors)
Non-repudiation – Ability to bind a human to a digital document
Privacy – Hot topic over the last 2 years due to NSA and Snowden. Challenges are not new.
Encryption – Encryption at rest, in transit, challenges: weak algorithms
Encryption at rest – Bitlocker, EFS, SQL TDE
Encryption in transit – SSL/TLS, IPsec, Office 365 message encryption
Azure RMS – AD RMS for On-Premises. Protect documents from Birth to end of life. Protection regardless of location.
Speaker goes over symmetrical, asymmetrical encryption, hardware security modules (HSM) technologies such as AES and shows how they work.
What is hashing? Uniquely identify a stream of data. It’s a one way function.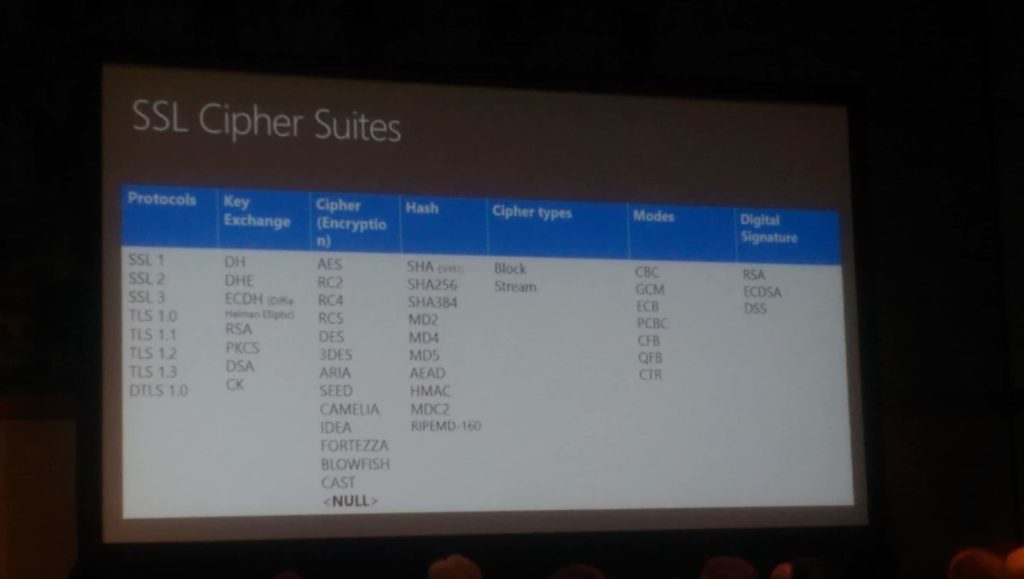
Use the tool IIS Crypto to disable/enable and change the order that ciphers are use. FREE.
Good ideas: Remove RC4, reorder suites, Update to 2012 R2, research ECC vs. RSA
Talks about Certificate Authorities, certificates, and their basic properties. Also discusses path of trust, and where to find certificates in Windows.
CA Lifetime planning: End certs – 2 years, intermediate CA – 4 years, root CA – 8 years. Renew certificates when 50% of their life has expired.
S/MIME – For Email encryption and digital signatures